A typical best practice on Windows for unattended applications – services, batch jobs, etc. – is to run those applications using a separate, less privileged user login. But you will likely run into situations where you really need to run your application interactively as that separate login. While there are other workarounds like output redirection, sometimes it would be a lot faster and easier if you could do user impersonation in Windows, similar to sudo and su in Unix. Well it turns out you can! And there are several ways to do it.
Shift Right Click
A quick way to execute a program as another user in Windows is to hold down your shift key and right clicking on the program or shortcut. Doing so will cause a new context menu item to appear: “Run as different user…”
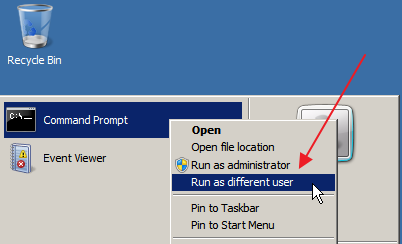
If you click on this menu option you’ll be presented with a dialog to enter the credentials for the user you want to run the program as. You can even specify machine local usernames (<machinename>\<username>) from here.
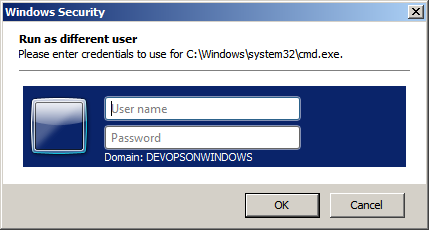
After entering the other user’s credentials you’ll be executing that program as that other user.
RunAs
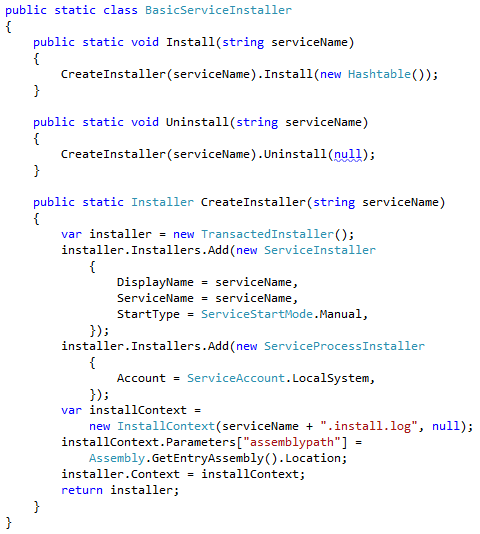
The built-in Windows RunAs command is another way to do user impersonation in Windows. Typically you would execute RunAs like: runas /user:<domain>\<username> “<command and arguments>” like:
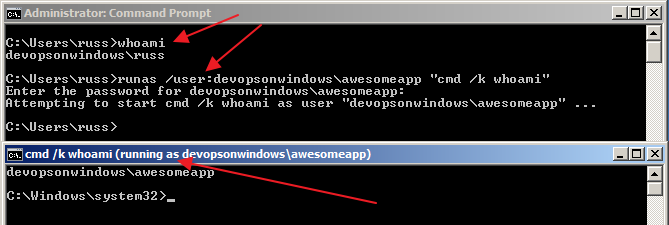
RunAs takes a username and a command line (among other things) and executes the given command as the given user (after you enter the user’s password of course). Run “runas /?’ for full details.
PsExec
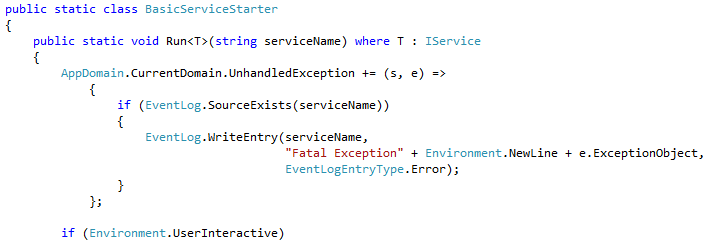
If you’ve read some of our other articles you know by now that we’re big fans of the SysInternals PsTools suite. PsExec is one of these tools that not only can be used for remote process execution (like we’ve discussed before) but can also be used to locally execute a process using another user’s credentials.
Typically you would execute PsExec like: PsExec -u <domain>\<username> <command> “<arguments>”
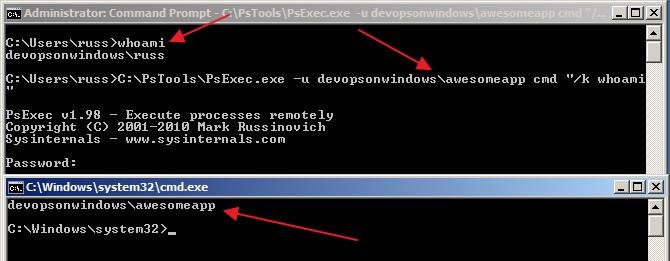
Download and run “PsExec -?” for full details. Note: you can also pass in a password via the command line with PsExec. Be careful with this as users with access to the system and access to see all executing processes on the system can easily see the username and password from your PsExec command line by looking at the process tree on the system.
PowerShell Start-Process
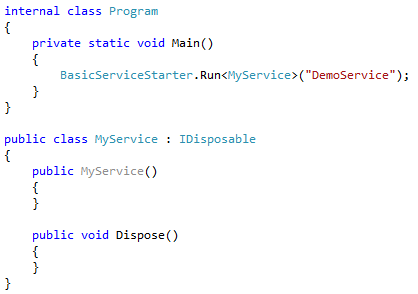
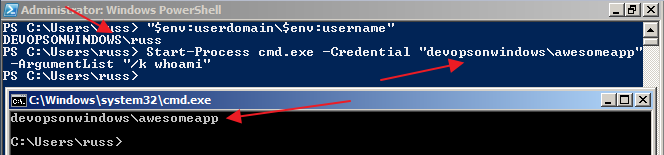
PowerShell has a Start-Process cmdlet that can also be used for user impersonation in Windows. You can accomplish this by using the cmdlet like:
Start-Process <command> -Credential “<domain>\<username>” -ArgumentList “<command arguments>”
So as you can see, there are plenty of options for user impersonation in Windows. Do you know of other ways? Leave a comment and let us know.